Checkpoint Mobile Access Blade and AUTH.AS Integration Manual
This manual describes how to integrate AUTH.AS service as the user authentication platform in CheckPoint Mobile Access VPN.
The manual assumes following several steps, done via SmartDashboard connected to CheckPoint management server with administrator privileges or to the gateway itself when standalone configuration is used.
1. Enabling Mobile Access and IPSec VPN blades in the gateway config
At this stage it is necessary to activate Mobile Access and IPSec VPN blades on the gateway to which users will connect.
You can do this in the Network Security tab on General Properties screen:
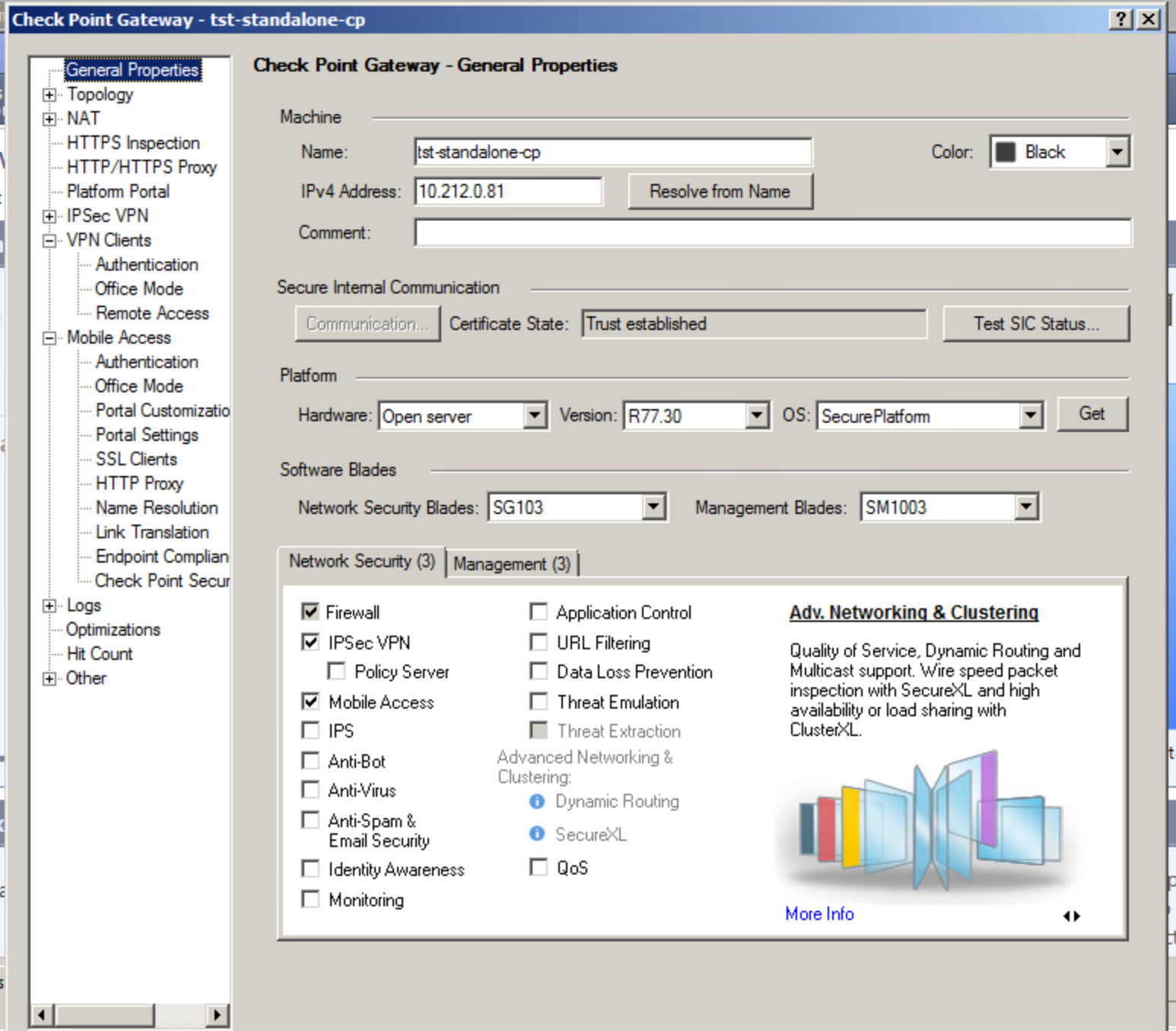
Check the Mobile Access box and a window will appear where you must select Mobile Access features you are planning to use. This manual covers the procedures for connecting users via Endpoint Security VPN.
There is an option to use auth.as also with mobile clients authentication, for example, when using CheckPoint Capsule VPN. To do this, mobile devices support should be enabled together with the related remote access software, in Mobile Access blade settings, like it's shown below:
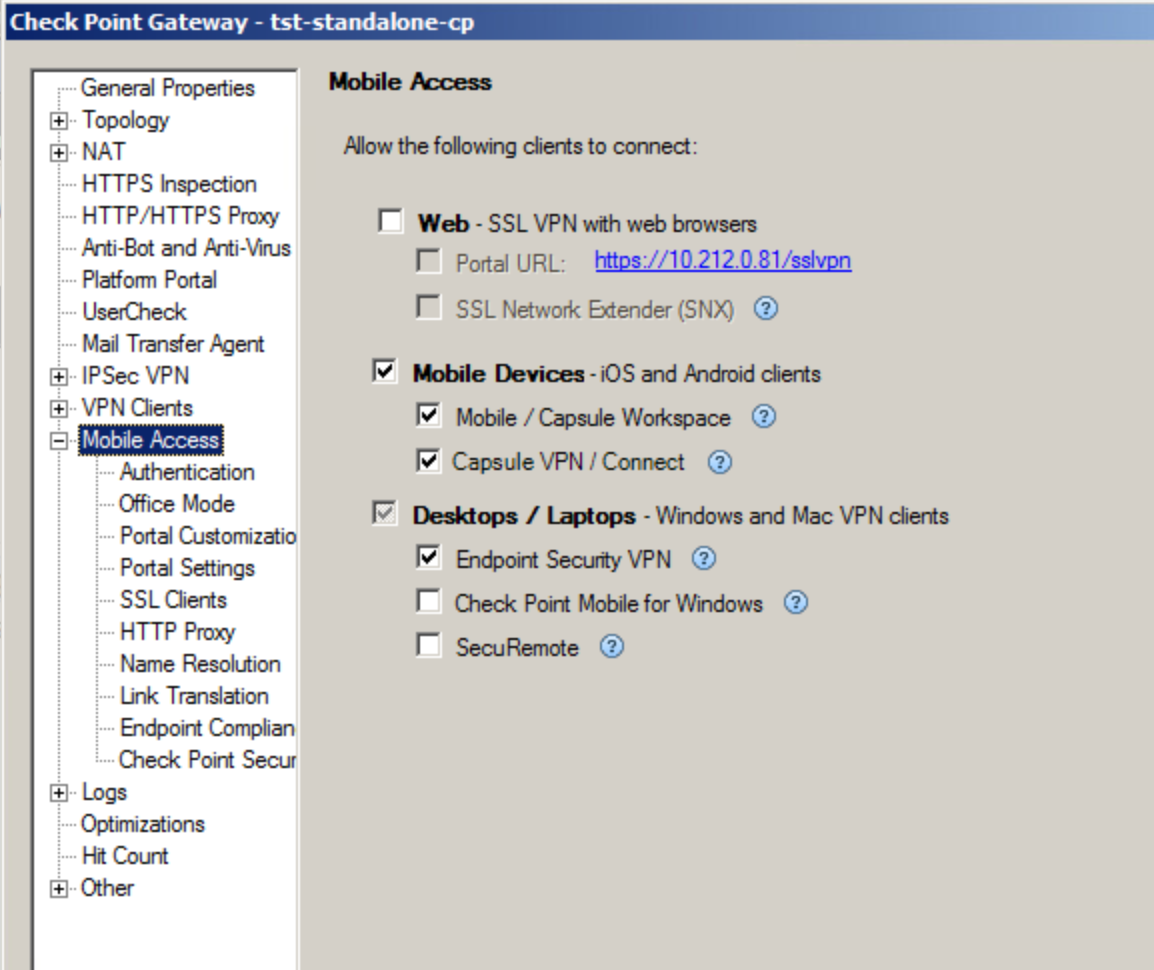
AD DS connection is not mandatory when integrating AUTH.AS service and Mobile Access VPN.
2. Specifying RADIUS server as authentication source for VPN clients
2.1. Selecting via SmartDashboard the RADIUS server to be used:
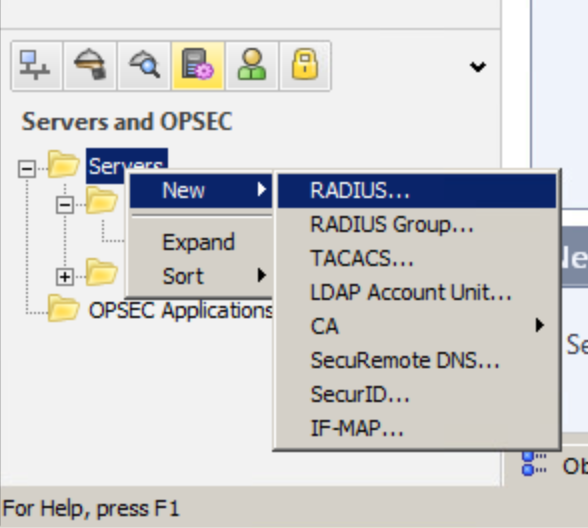
In order to use RADIUS for authorization, you must go to SmartDashboard and specify servers that will be used. Select “RADIUS..”. from the menu (see the screenshot).
2.2. Specifying configuration of the RADIUS server to be detected:
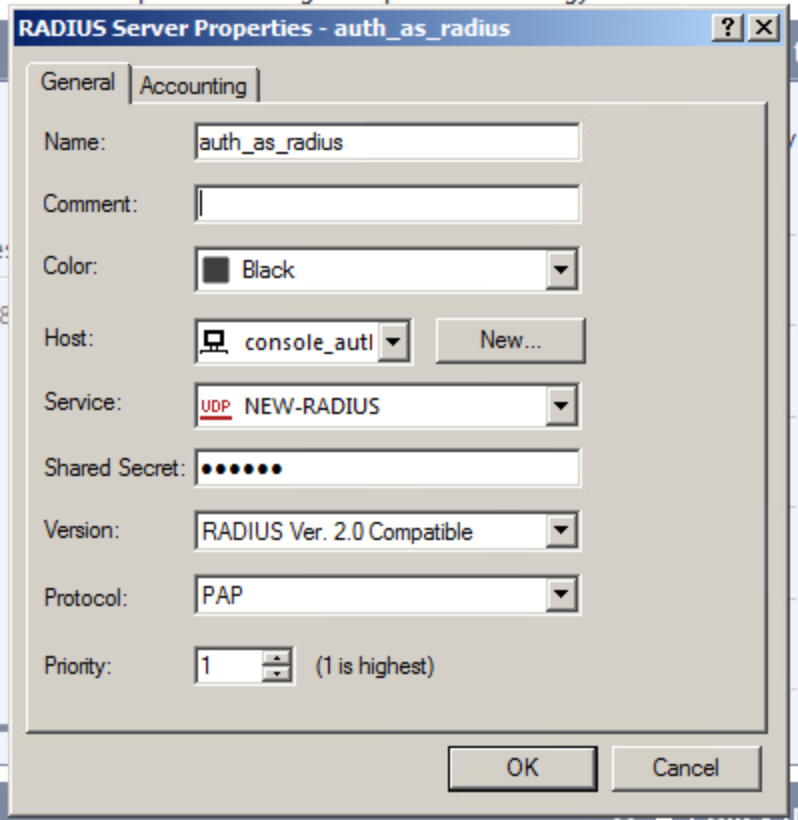
Create a new Host and specify the IP address of the RADIUS server to be detected.
Keep in mind that RADIUS and NEW-RADIUS services use different ports in CheckPoint.
Note:
To ensure fault tolerance it is recommended to use a group of RADIUS servers. Add all servers and go to New -> RADIUS Group menu
2.3. Selecting external profile for users to whom configurable RADIUS authentication will be applied.
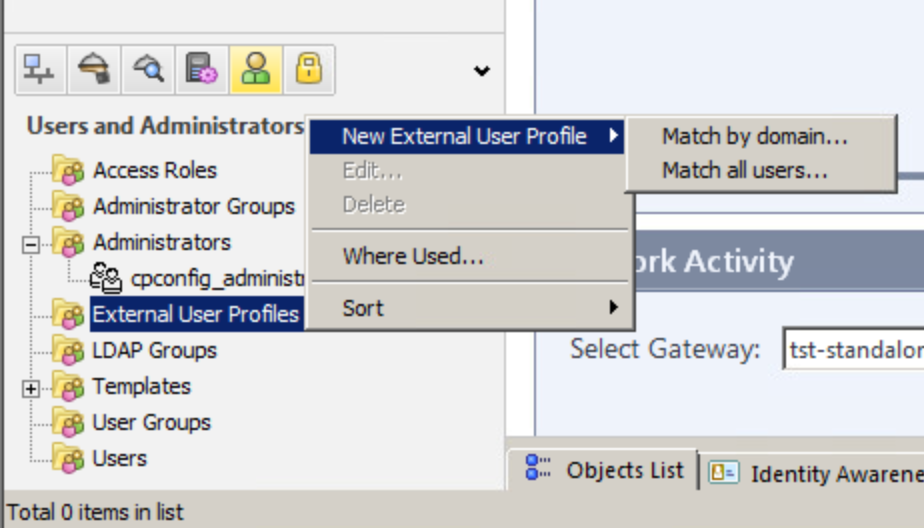
There are two ways - one is to create external profile for all users and another is to create a profile tied to a specific domain.
First option will authenticate users attempting to connect to VPN via an external source (or RADIUS servers with AUTH.AS, in our case).
Second option allows you to explicitly specify a domain (and a method to split username and domain), for which this type of authentication will be used.
Both options are configured in almost the same way.
Regardless of a profile type, you must specify the type of authentication source, in our case it is a server or a group of RADIUS servers with AUTH.AS:
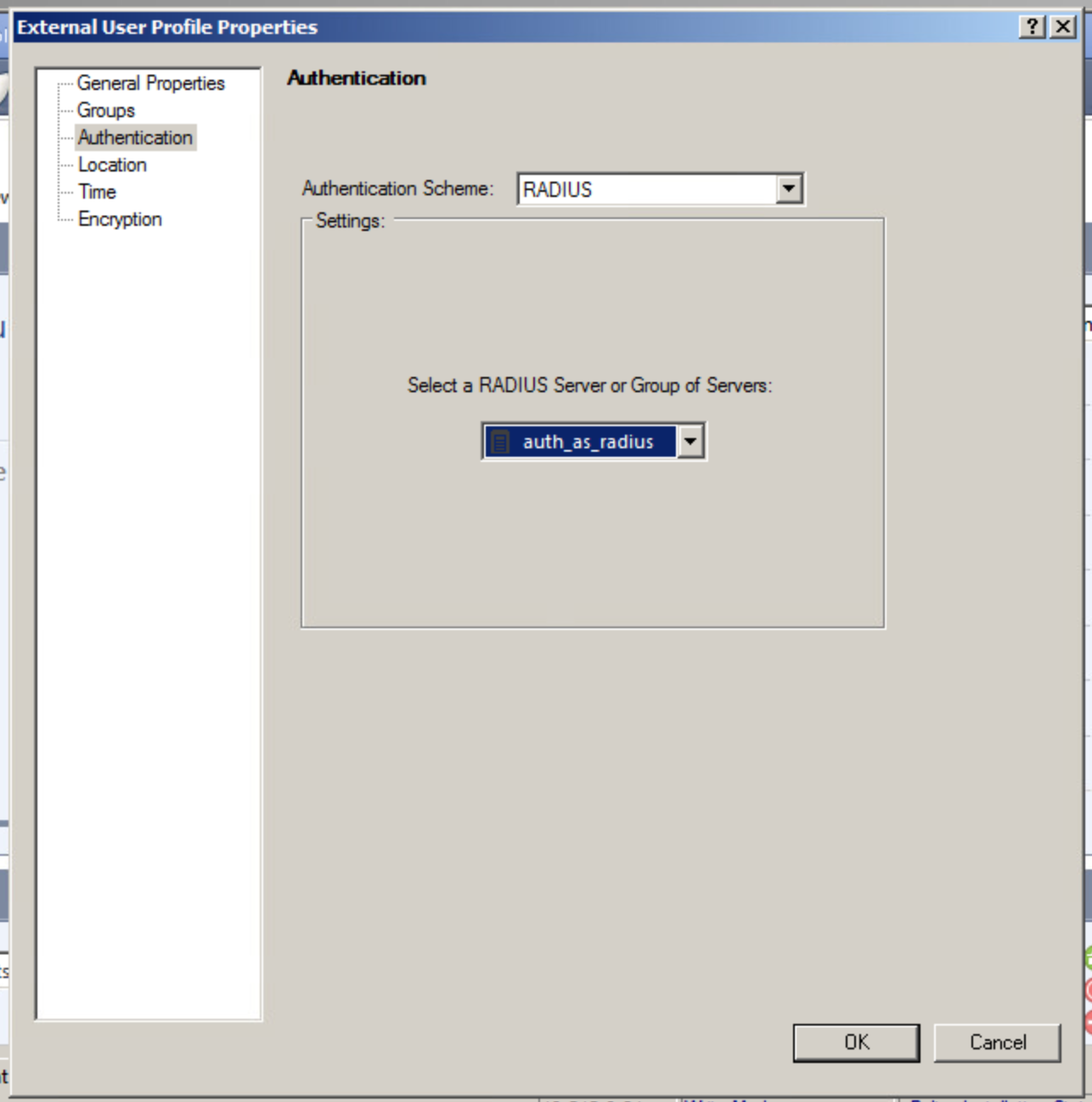
Skipping this step may cause “Unknown user” errors when trying to connect a VPN-client.
2.4. Enabling RADIUS authentication for Mobile Access and IPSec VPN blades.
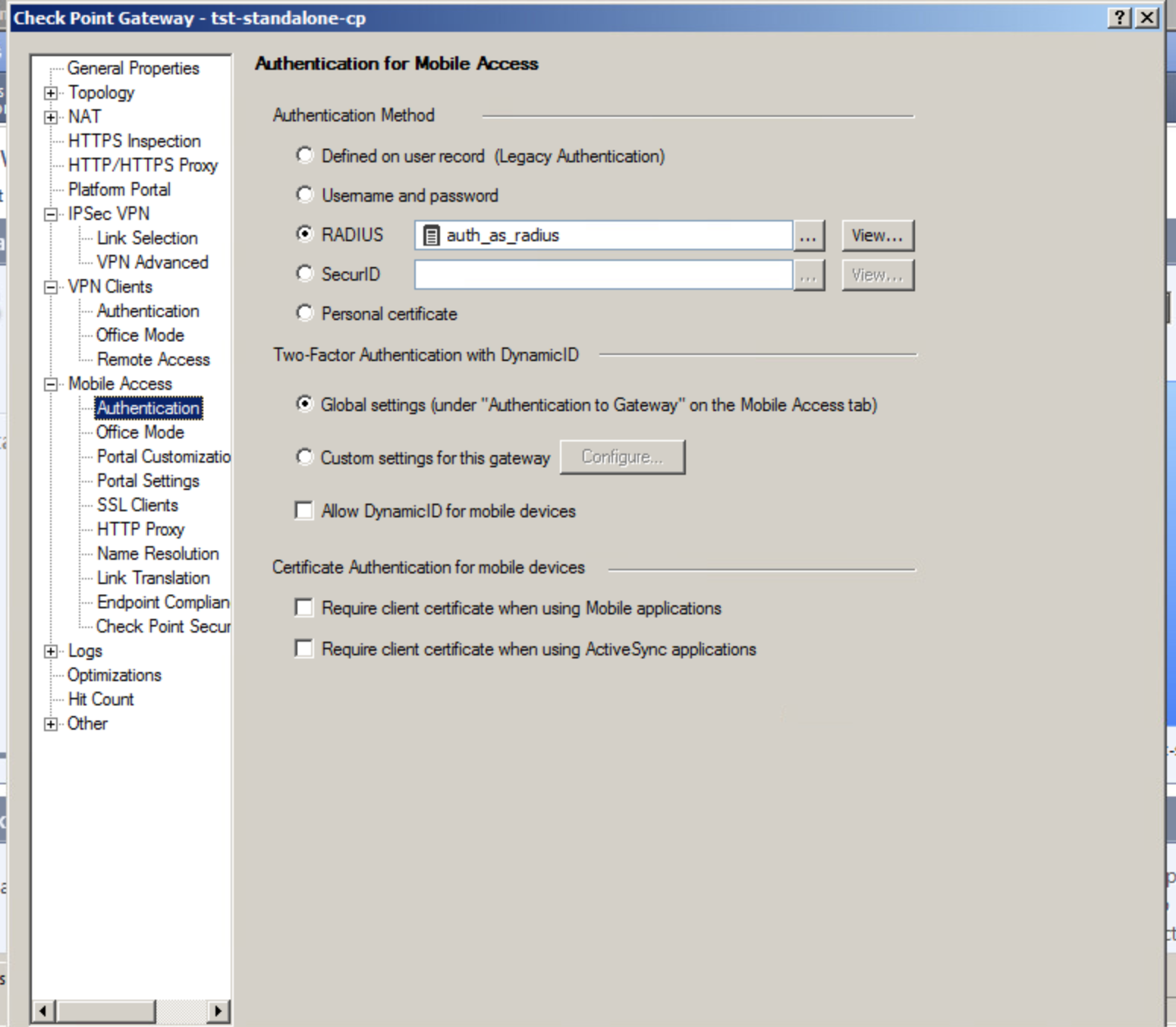
In this step you must specify the RADIUS server (or the group of servers) which we have added in previous steps as the authentication source for Mobile Access blade./p>
The same server must be specified in the VPN Clients -> Authentication tab.
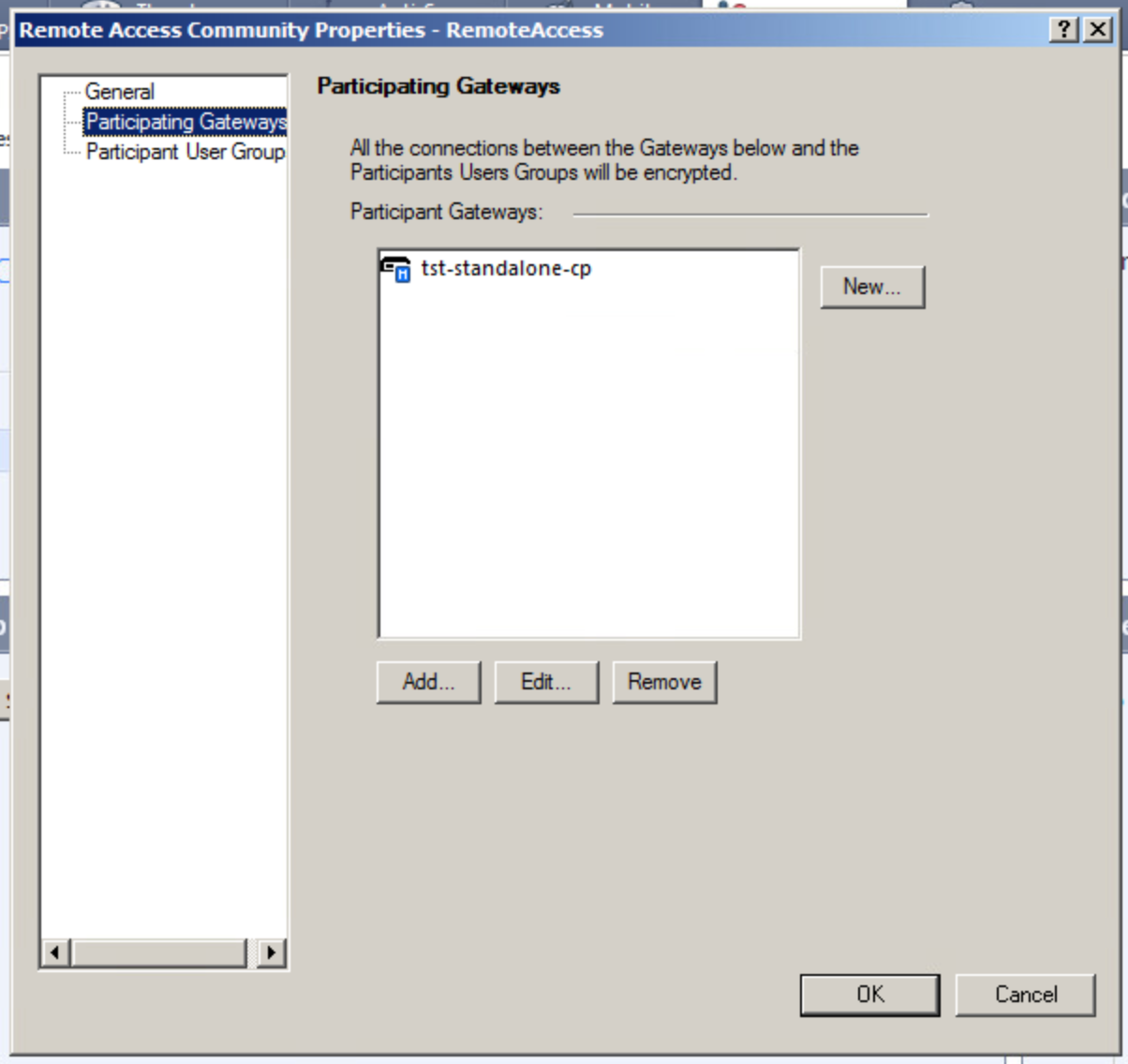
3. Adding a gateway in Remote Access VPN Community
After completing all above-mentioned steps you must add a gateway in Remote Access VPN Community. Do this in IPSec VPN Smart Dashboard settings:
After you complete all these steps you can use CheckPoint Mobile Access VPN with AUTH.AS two-factor authentication service:
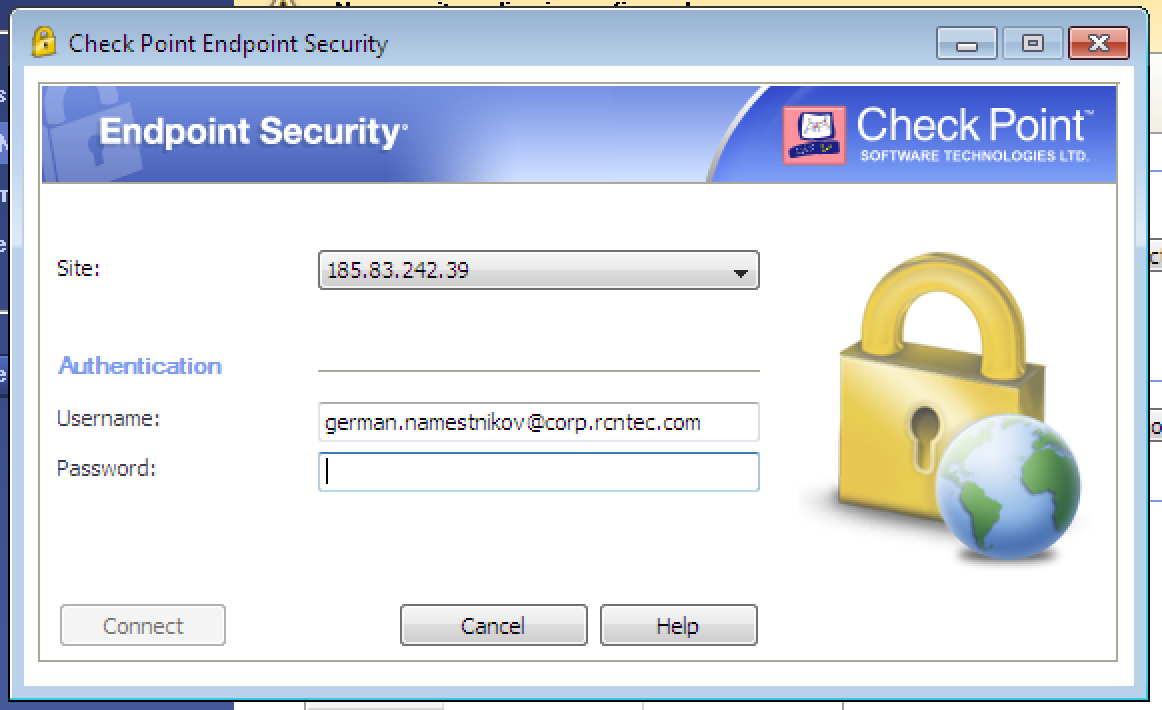
To connect, enter your login to the “Username” field, then your password and six digits from your auth.as:token mobile app to the “Password” field. Instructions for downloading the app and configuring it for generating your own tokens are sent to e-mail after the user is registered in AUTH.AS system. Type two passwords in a row, without any spaces between them, and hit "Connect".
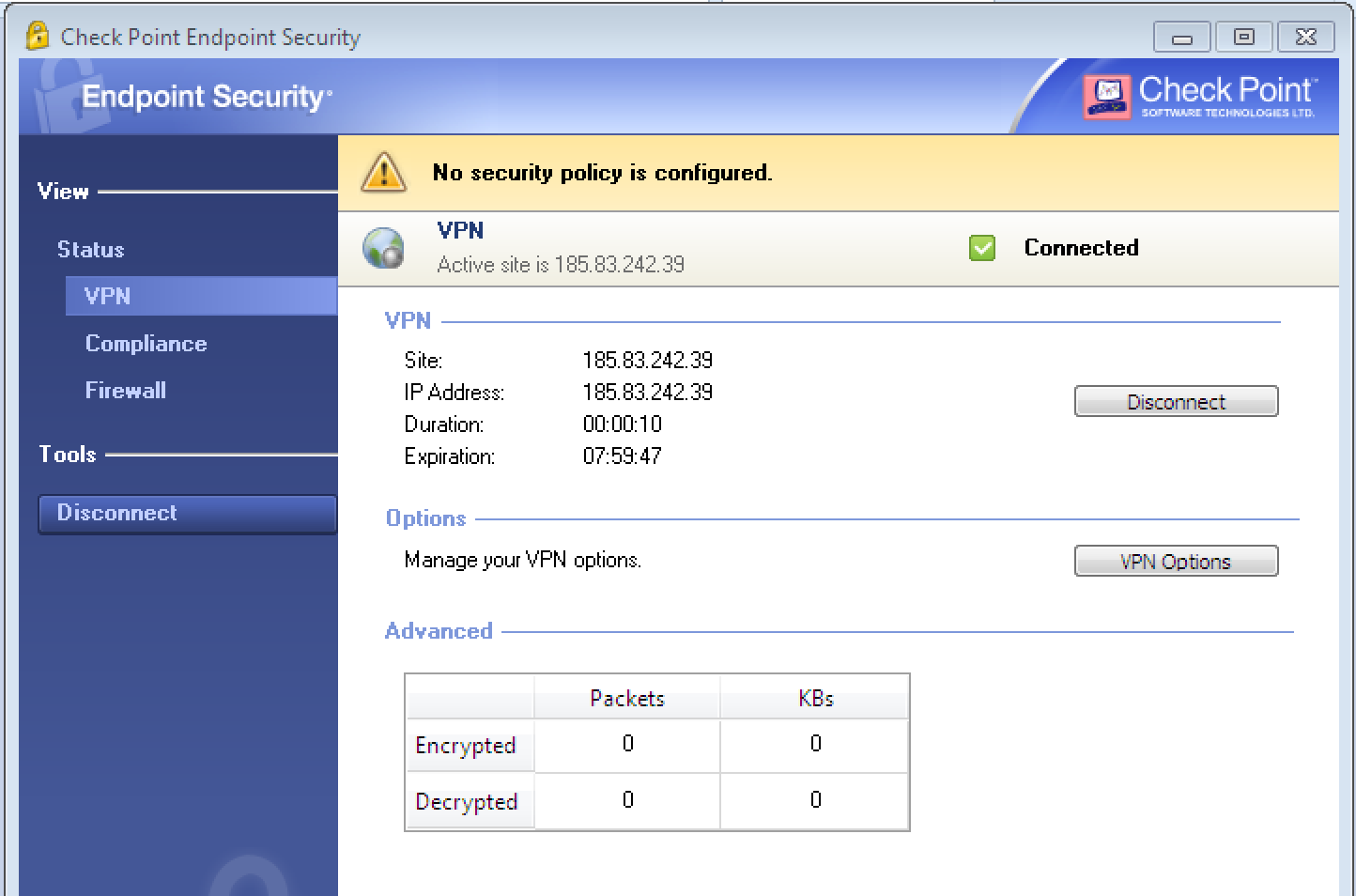
You will see that the connection was successful.


